04. Hacking Lifecycle
Hacking Lifecycle
ND545 C1 L3 04 Hacking Lifecycle Video
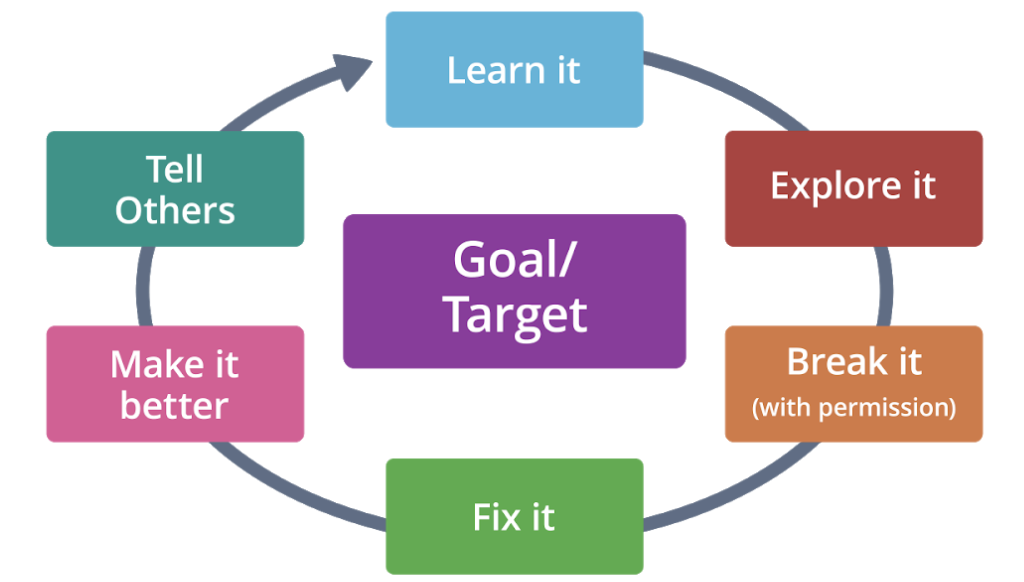
Hacking Lifecycle
Throughout history, hackers have followed the same lifecycle process:
- A target or goal: understand why you are assessing it’s security.
- Learn it: learn as much as you can about it
- Explore it: understand how it works and what others know about it. This is known as reconnaissance.
- Break it: understand the target’s weaknesses or vulnerabilities.
- Fix it: secure operating systems, applications and networks.
- Make it better: figure out a better way to secure the asset.
- Tell others: tell others what we find. It’s called ethical disclosure.
This is in order to categorize assets, risks, threats, vulnerabilities, and exploits affecting computer systems
New terms
- Asset: A major application, general support system, high impact program, physical plant, mission-critical system, personnel, equipment, or a logically related group of systems.
- Vulnerability: Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat
- Threat: Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service
- Risk: A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: (i) the adverse impacts that would arise if the circumstance or event occurs; and (ii) the likelihood of occurrence
- Penetration Testing: A test methodology in which assessors, typically working under specific constraints, attempt to circumvent or defeat the security features of an information system.
Source: https://csrc.nist.gov/glossary/
Further research
- The Jargon File contains a more thorough explanation of the hacking lifecycle including a comprehensive glossary of hacking terms.
- If you enjoy history and want to learn more about original hackers, read How To Become A Hacker by Eric Steven Raymond found at http://www.catb.org/~esr/faqs/hacker-howto.html.
You can also read The Jargon File at http://www.catb.org/jargon/, which is "a comprehensive compendium of hacker slang illuminating many aspects of hackish tradition, folklore, and humor."